Recommendations
2025-03-21
Enterprise Smart and Efficient Settlement
2025-03-21
ESB System Integration Service Platform
2025-03-07
MDM Master Data Management Platform
Supplier Invoice Management
 2025-03-21
|Proprietary Product Solutions
2025-03-21
|Proprietary Product Solutions
Project Background: Traditional finance and tax management in current business operations has significant pain points: offline reconciliation is labor-intensive, with low collaboration efficiency and rough management, leading to increased costs and risks; the entire invoice processing workflow is manual (verification, entry, scanning, authentication), with a large amount of repetitive work that is prone to errors and disconnected from business systems, causing redundant processes; with stricter tax compliance requirements, the risk of supplier invoice compliance is increasing, and the data silos between finance and business data lead to information lag, affecting settlement efficiency, especially during the peak settlement period at the end of the month; additionally, manual invoicing can cause data gaps and poor coordination across the supply chain. To address these challenges, there is an urgent need to reconstruct finance and tax processes through intelligent means.
Solutions:
1. Invoice Data Transmission Encryption
During invoice data transmission, use encryption protocols such as SSL/TLS to encapsulate and encrypt data, preventing data from being stolen or altered during transmission.
Regularly update encryption algorithms and keys to ensure encryption strength meets current security requirements and addresses evolving cyberattack methods.
2. User Identity Authentication
Use multi-factor authentication methods, such as usernames/passwords, SMS verification codes, and digital certificates, to authenticate users of the invoicing system, ensuring only legitimate users can log in.
Establish a user identity information database to record basic and permission information, providing a basis for identity authentication and permission management.
3. Access Control Policy
Assign different permissions based on user roles and responsibilities, such as invoicing, inquiry, and review permissions, to implement the principle of least privilege.
4. Log Auditing and Monitoring
Conduct real-time monitoring and auditing of access to the invoicing system, recording user access and operation details for traceability and analysis in the event of a security incident.
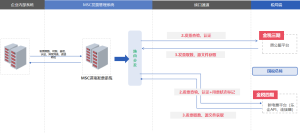
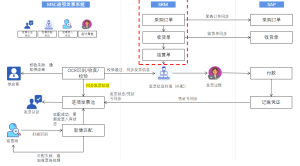
System Function – Data Acquisition:
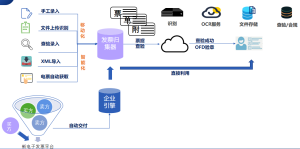
Implementation Effect: